By Samuel Rubenfeld
December 5, 2019
This report has been updated with additional information from the U.S. and U.K. governments, a statement from the Russian government and research by Kharon.
Evil Corp, a Russia-based cybercriminal organization, was sanctioned and two of its leading members were indicted in the U.S., authorities in the U.K. and U.S. announced Thursday.
The sanctions designations and criminal charges follow a decade-long cybercrime, hacking and fraud spree involving the theft of at least USD 170 million across more than 40 countries, authorities said at a press conference in Washington, D.C., and in statements to the media.
Maksim Yakubets, a 32-year-old from Moscow who has used multiple online aliases, including “aqua,” is Evil Corp’s leader, officials said. He drives a customized Lamborghini supercar with a personalized number plate that translates to “thief” and spent more than a quarter-million pounds on his wedding, according to a statement from the U.K. National Crime Agency (NCA). The NCA also posted photos and videos of Yakubets on social media, highlighting his lifestyle.
Yakubets, in addition to being sanctioned, was also indicted and charged in a separate criminal complaint, both unsealed Thursday by U.S. prosecutors. And the U.S. State Department announced a USD 5 million reward for information leading to his arrest, which prosecutors said was the largest reward offer to date for a suspected cybercriminal.


“Yakubets and the members of his criminal networks devised and implemented the kinds of criminal schemes so audacious and sophisticated that they would be difficult to imagine if they were not real,” said Assistant Attorney General Brian A. Benczkowski at the press conference.
Anatoly Antonov, the Russian ambassador to the U.S., responded to the sanctions and criminal charges with a post on the embassy’s Facebook page, saying there was no proof to support the U.S. allegations. “We’ve been long suggesting to the U.S. side to establish a direct dialogue on cybersecurity issues, reach an accord on a joint response to the corresponding threats. However, Washington deliberately ignores this idea,” he said in the post.
“Such rhetoric clearly does not help [the] stabilization of bilateral relations,” Antonov said.
U.S. prosecutors said Evil Corp was behind a malware called “Bugat,” which was designed to automate the theft of confidential personal and financial information, such as online banking credentials, from infected computers. A later version known as “Dridex” was designed to assist with installing ransomware, prosecutors said. The U.S. Treasury Department and the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) on Thursday issued guidance about the malware that included “indicators of compromise” — email and IP addresses — associated with Dridex, and its use against the financial services sector.
The malware is typically distributed through phishing email campaigns, the guidance said. Though the highest infection rates took place in late 2015 and early 2016, it continues to affect numerous countries, the majority of which are English-speaking, according to the guidance.
Bugat, and a second malware allegedly distributed by Yakubets called “Zeus,” made unauthorized wire transfers from victims’ bank accounts, prosecutors said. They then used so-called “money mules” to receive the funds into their bank accounts, and then moved the money to other accounts to withdraw the funds and transport them overseas as bulk cash, prosecutors said. They also used a botnet to further the scheme, according to prosecutors. (The U.S. Justice Department and Europol announced actions this week against money mules.)
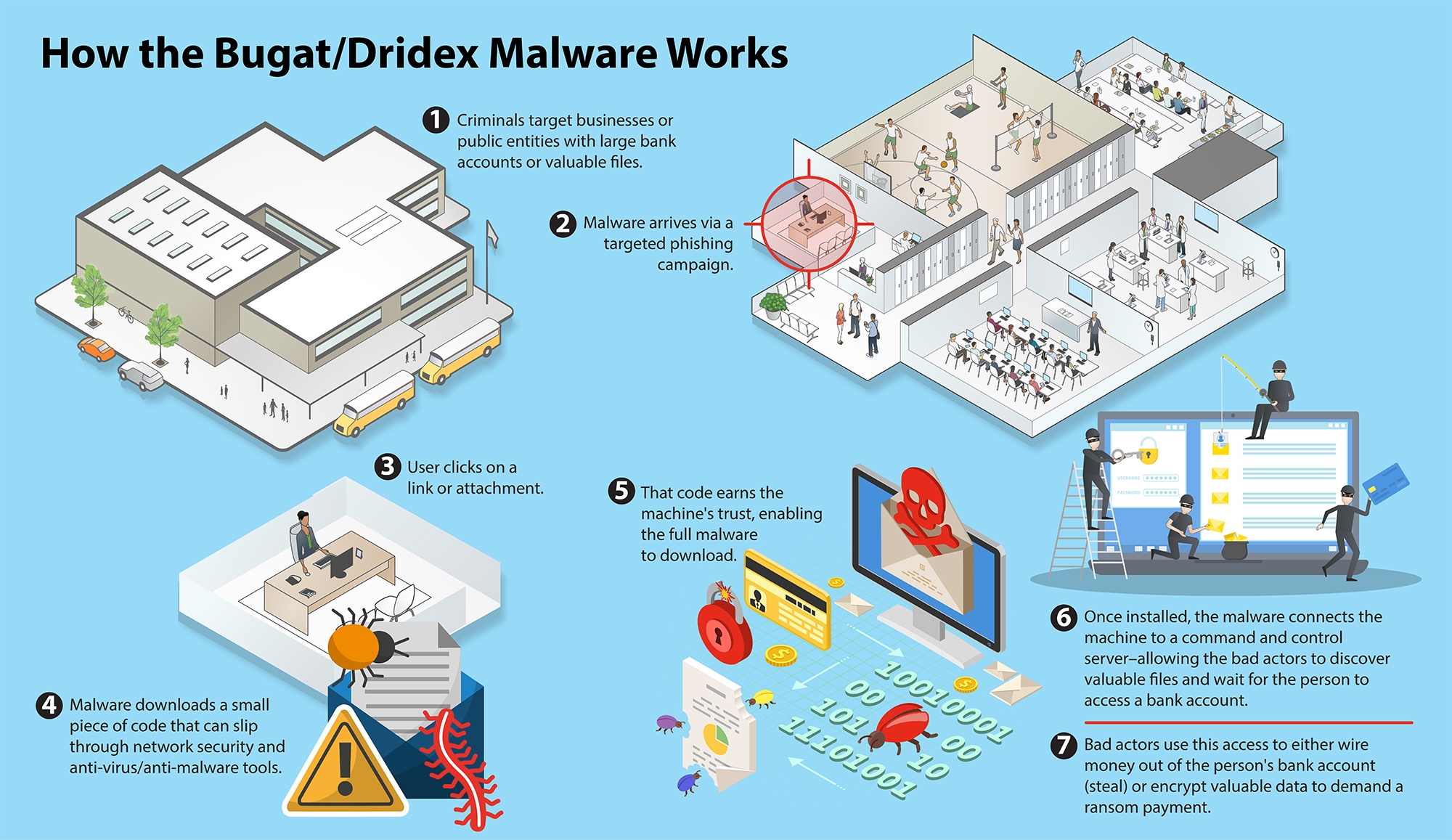
Dridex led to the theft of at least USD 100 million, the Treasury said, warning that the amount could be significantly higher. Prosecutors estimated the losses associated with Zeus to be USD 70 million.
Many of the victims were small and mid-sized businesses whose bank accounts typically don’t have the same legal protections as a consumer accounts, so some of the losses were “particularly devastating,” Benczkowski said. Banks, a school district, several companies, non-profit organizations and a religious congregation were victims of either Zeus or Bugat, according to court documents cited by prosecutors.
Prior to Evil Corp, Yakubets was associated with Evgeniy Bogachev, who was sanctioned in December 2016 for the distribution of Zeus, Jabber Zeus and GameOver Zeus malware schemes, the Treasury said. Bogachev was directly responsible for the development and use of Cryptolocker, a form of ransomware known to have held over 120,000 U.S. victims’ data hostage for financial gain, the Treasury said when he was designated.
Yakubets was responsible for recruiting and managing a network of people who facilitated transfers of funds gained through Bogachev’s efforts, according to the Treasury. In addition to his leadership role at Evil Corp, Yakubets was working, as of 2017, for the Russian Federal Security Service (FSB), the Treasury said. As of April 2018, he was in the process of obtaining a license to work with Russian classified information from the FSB, according to the Treasury.
The Treasury sanctioned a total of 17 people and seven entities as part of the Evil Corp network, including Igor Turashev, who authorities said served as an administrator for Yakubets; he was charged alongside Yakubets in the indictment unsealed Thursday.
“Our goal is to shut down Evil Corp, deter the distribution of Dridex, target the ‘money mule’ network used to transfer stolen funds, and ultimately to protect our citizens from the group’s criminal activities,” said Treasury Secretary Steven Mnuchin.
Denis Gusev, who the Treasury said has served as of 2018 as a financial facilitator for Evil Corp, was also sanctioned, along with six companies for which he serves as general director. Owners and managers of the six sanctioned companies linked to Gusev are tied to at least 10 entities not mentioned in the Treasury’s statement that are active in a variety of economic sectors, according to corporate records. Gusev is also the director general of Snabstroy OOO, a Moscow-based building construction company that was not sanctioned, records show. He owns Promresurs OOO, a Western Siberia-based company involved in the maintenance and repair of motor vehicles, according to corporate records.
BBC Russian reached Gusev for comment after the release of the Treasury’s designation statement. “No need to be familiar with my business! In general, you don’t need to know anything about me," he was quoted as saying.
Additional members and financial facilitators of Evil Corp were also designated, including those who carry out the group’s critical logistical, technical, and financial functions, the Treasury said.
Thursday’s actions are the latest efforts taken by the U.S. and U.K. against Evil Corp and its surrounding network. U.S. prosecutors in 2015 charged Andrey Ghinkul, a Moldovan man, for administering Bugat. Ghinkul was arrested in Cyprus, and extradited to the U.S. in February 2016. He pleaded guilty in February 2017 and was sentenced in December 2018 to time served.
The U.S. and the U.K. disrupted the Evil Corp infrastructure at the time of Ghinkul’s arrest, but U.K. authorities said Thursday that Evil Corp was able to adapt the malware within weeks and resume its activities. Investigations in the U.K. have also targeted Yakubets’ network of money launderers who funneled profits back to Evil Corp, the NCA said, adding that eight people who have been sentenced to a total of more than 40 years in prison.
Analysts from the Eurasia team contributed to this report.







